Charting Your IT Certification Pathway
Creating a Plan Has Never Been Easier with Today’s Online Tools
By Tom Kennedy
“Failing to plan is planning to fail.”
It’s a quote that has been used for countless business leadership presentations and sports stories. Nonetheless, these simple, but meaningful words from Benjamin Franklin are so relevant in today’s IT world.
Last month, we wrote about “Why Certifications Matter.” Today’s article speaks to the practical cybersecurity pathway you can map out based on where you’ve been, your natural talents and where you want to go. The good news is that there are many sophisticated online tools to help you create the right plan.
Determining your destination is a critical first step. Our advisors at ComputerMinds.Com recommend starting at CyberSeek. CyberSeek, whose mission it is to “help close the cybersecurity skills gap by providing detailed, actionable data about supply and demand in the cybersecurity job market,” is a joint project between the National Initiative for Cybersecurity Education (NICE), The Computing Technology Industry Association (CompTIA), and Burning Glass Technologies. The site provides excellent tools for job seekers and current workers, students, and employers.
One of the first features visitors will notice is the ability to see a state-by-state cybersecurity demand and supply market view. The interactive heat map section allows you to drill down to the metro area level to see both the challenges and opportunities facing your local cybersecurity workforce. (Download cyberseek_infographic.)
Clicking on a state like Texas, for example, tells us that there are a total of 47,276 cybersecurity job openings in the state (using data from October 2019 through September 2020). We can also see that there were 78,636 estimated cybersecurity workers employed in the state during that same period. The top job titles requested by employers within the cybersecurity job market in Texas included:
- Cyber Security Engineer
- Cyber Security Analyst
- Cyber Security Consultant
- Software Developer / Engineer
- Systems Engineer
- Cyber Security Manager / Administrator
- Network Engineer / Architect
- Vulnerability Analyst / Penetration Tester
- IT Auditor
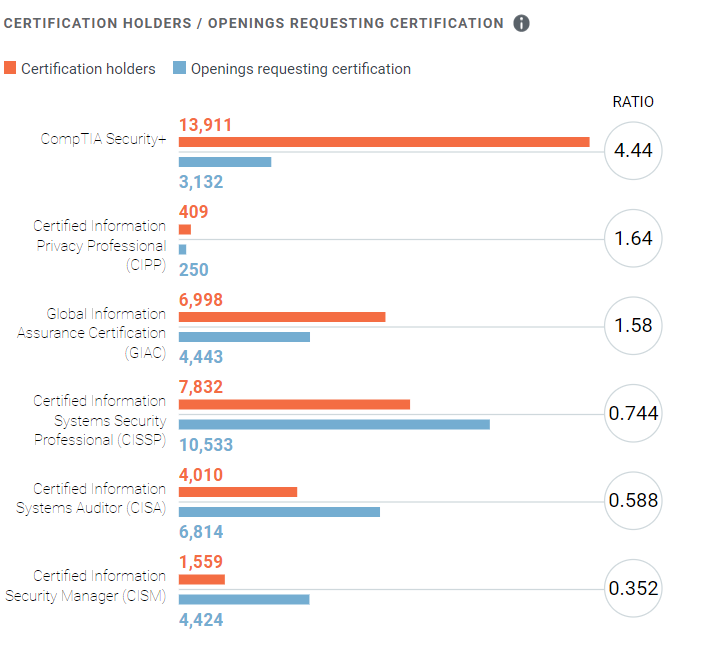
Another box illustrates the ratio of current holders of common cybersecurity-related certifications to job openings for each certification. In the diagram below, for example, we see that demand (job openings) for Certified Information Security Professionals (CISSP) is outpacing certification holders by a significant margin.
Further, you can slice and dice your view of a state by public sector data and private sector data. The private sector data allows you to take a look at demand and supply in specific vertical markets, such as Educational Services, Financial Services, and Construction, as examples. The Educational Services private sector data in Texas, for instance, indicates a “very low” supply of cybersecurity workers relative to demand in a particular location.
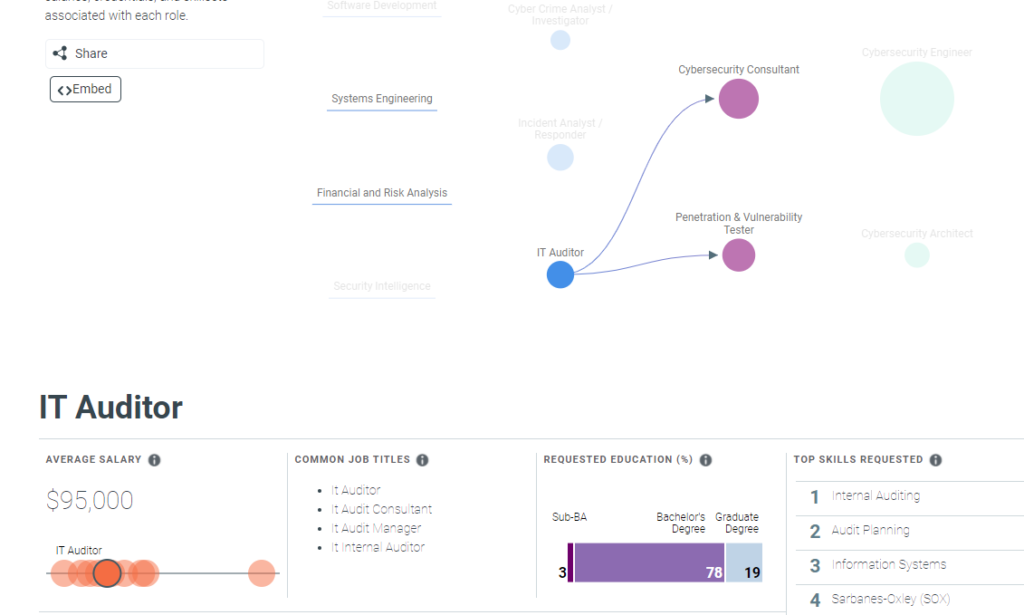
Besides the “Interactive Map,” the other part of this valuable tool is the “Career Pathway” tab. From this location you can see that there are many opportunities for workers to start and advance their careers within cybersecurity. It illustrates jobs within cybersecurity, common transition opportunities between them, and detailed information about the salaries, credentials, and skills associated with each role. Hovering over an entry-level position like Cybersecurity Specialist / Technician, for example, yields current job openings and average salaries, plus logical pathways to mid-level positions as Cybersecurity Analyst, Cybersecurity Consultant, Penetration and Vulnerability Tester. Hovering on the mid-level positions then provides information and pathways to advanced-level positions.
Drilling down into an entry-level position like IT Auditor (see following screen shot), delivers information about total job openings, average salary, common job titles, education requirements and certification requirements.
All in all, CyberSeeks offers a great tool to envision your future in cybersecurity. In an uncertain world, it provides job seekers and current workers visibility into market demand for specific positions and transition pathways to your career objective.
“It’s a great resource to understand where you might want to go with your career,” says Prabath Boteju, founder of IT training company ComputerMinds.Com. “It helps educate job seekers and current workers with solid facts.”
“No matter where you’ve been with your career, it gives you a good tool to figure out how you might fit in with the cybersecurity world. Whether you’ve been a teacher or a project manager or a marketing manager, this is a great resource to help you transition into a cybersecurity role. You don’t necessarily have to have a history in IT to pivot into cybersecurity.”
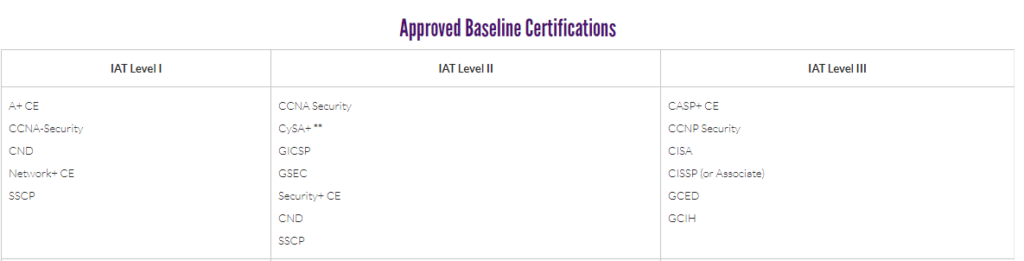
Now that you know where you want to go, the question is how to map out the pathway to get there. The DoD Cyber Exchange website provides excellent guidance toward this end, whether you are interested in a career in the public sector, or with a business that contracts with the public sector. The site has a page dedicated to DoD Approved 8570 Baseline Certifications provides Information Assurance (IA) certifications to meet the US Department of Defense requirements we talked about in last month’s blog article. As discussed, the DoD has published a number of directives that set out the requirements of their workforce, and the workforce of contractors doing business with the DoD. The image below illustrates certifications required at three levels of the Information Assurance Technical (IAT) role.
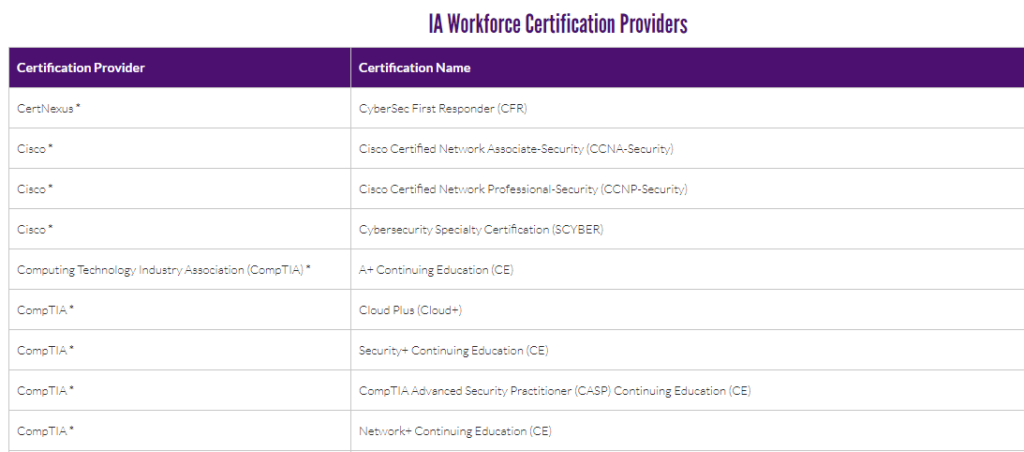
Further down this page, a second table delineates the certification providers associated with each approved certification. Here’s a snapshot of this table:
“We use this as a guide with our students,” adds Boteju. “It comes down to what you are targeting, knowing where you want to go and then mapping out the certifications you need to get there. We use this list because it’s recognized by the federal government and recognized by the government contractors. It eliminates the guesswork.”
Often job seekers and current workers in the IT field do not think about what the logical path looks like to get to that next level. The tools described here are excellent resources to get started.
“We really want to understand where the student has been, their skills, and interests before prescribing a certification path,” notes Boteju. “It’s never too late to make a career transition or professional pivot, or to seek a promotion. However, planning is essential. We help our students focus on a plan that accounts for their natural skills, interests and experiences, plus has the right certification pathway to get them to where they want to go.”
If you have any questions or would like to get more information about ComputerMinds.Com, please give them a call at: (817) 944-7348 or (682) 259-8033, or check out the contact us portion of the website: https://computerminds.com/contact/
In an upcoming article related to this topic, we will lay out some of the important certification resources available to IT-career-minded students as they map out career pathways.
About ComputerMinds.Com
Based in the Dallas Fort Worth metro area, ComputerMinds.Com specializes in cybersecurity training, project management, and logistics and supply chain management, to prepare students for prosperous careers in these growing industries. ComputerMinds.Com offers a broad range of certifications and hands-on career training, including CompTIA and Microsoft IT courses.




Leave a Reply
Want to join the discussion?Feel free to contribute!